Web Application Penetration Testing Explained
Web application penetration testing entails detailed scrutiny of web applications to uncover vulnerabilities susceptible to cyber attacker exploitation. This testing is crucial for pinpointing security gaps in web applications, which are often access points to critical data and business operations. Through controlled cyber attack simulations, testers can identify and evaluate the significance of various security deficiencies, including issues with input validation, server security configurations, authentication mechanisms, and cross-site scripting (XSS) vulnerabilities.
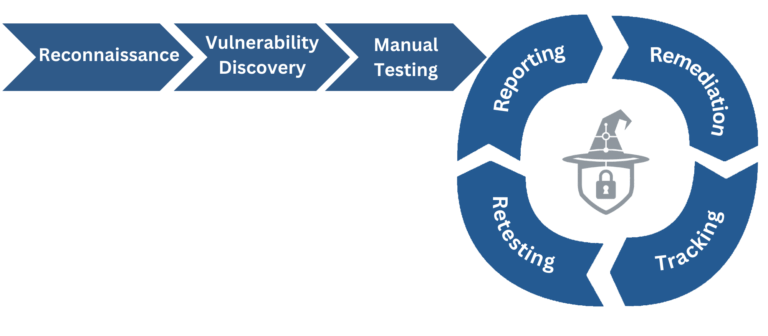
Reconnaissance
The reconnaissance phase is the first and foundational stage of web application penetration testing, aimed at thoroughly understanding the target application’s structure, features, and technology. This phase splits into passive and active reconnaissance. Passive reconnaissance involves non-intrusive data collection from sources like search engines, social media, and public records to gather information about the domain, network, IP addresses, and the organization’s online presence, using tools such as WHOIS and DNS queries for domain and hosting details.
Active reconnaissance requires direct interaction with the web application, mapping visible elements like file directories and identifying entry points such as login pages. It includes using web crawlers for structural mapping and fingerprinting to identify and analyze the web server, application frameworks, and backend technologies. This phase is crucial for identifying vulnerabilities and setting the stage for more detailed testing, with its thoroughness vital for guiding the direction of subsequent web application penetration testing stages.

Application and Business Logic Mapping
At this stage of web application penetration testing, testers focus on understanding the application’s specific features and how they align with business operations based on the OWASP methodology. This stage goes beyond the basic framework, examining how the application functions in various scenarios and its data processing, user input response, and action sequence handling. Testers mimic user interactions and use methods like form submissions, API interactions, and role-based testing to analyze the application’s logic flows and response patterns, crucial for detecting business logic vulnerabilities missed by automated tools.
Additionally, this phase includes evaluating the application from a business perspective to identify any logical inconsistencies or exploitable gaps. Testers assess features in terms of business functionality, such as how an e-commerce platform manages transactions and user accounts. This comprehensive analysis of both technical and business aspects allows testers to identify not only technical issues but also operational vulnerabilities, ensuring a thorough evaluation of the application in its real-world business context.
Automated Vulnerability Scan
During this phase of web application penetration testing, pentesters utilize specialized software to conduct systematic scans for recognized vulnerabilities. This phase efficiently uncovers a range of basic and common security issues, such as SQL injection, XSS, insecure configurations, and outdated software elements, through automated scanners that send varied inputs and analyze the application’s responses. While this approach quickly covers a substantial portion of the application and offers a broad view of its security status, it mainly identifies well-documented vulnerabilities with limited manual input.
Despite their importance, automated scans have shortcomings, notably their struggle to detect complex vulnerabilities that need a deeper understanding of the context and the potential for producing false positives or negatives. Thus, these scans are primarily an initial step, with the outcomes needing extensive examination and confirmation by expert testers. This phase is essential for preparing the groundwork for subsequent stages of penetration testing, where manual methods and expert analysis play a crucial role in uncovering and exploiting deeper, often missed vulnerabilities.
Manual Vulnerability Discovery, Testing and Exploitation

In this critical stage of web application penetration testing, the expertise and detailed knowledge of testers are crucial. They engage in manual testing to uncover and exploit weaknesses that might not be detected by automated tools. This process includes a detailed analysis of how the application responds to different inputs and user interactions, focusing on identifying complex vulnerabilities like business logic errors, access control problems, and timing issues. Such manual probing is essential for fully understanding the application’s vulnerabilities and their context, providing a more in-depth evaluation of their severity and potential impact.
More than just identifying vulnerabilities, this phase involves ethical hackers demonstrating the practical effects of these weaknesses in controlled environments, mimicking real-world attacker tactics. They conduct activities such as escalating user privileges, extracting sensitive data, or abusing application features to concretely illustrate the risks these vulnerabilities pose. This hands-on approach is critical for determining the need for immediate remediation. The insights gained in this phase are extremely valuable, helping organizations to effectively prioritize their security measures and enhance the resilience of their web applications against actual attacks.
Reporting
The Reporting phase is a critical concluding stage in web application penetration testing, involving the comprehensive documentation of test findings in a detailed report. The report provides a thorough overview of identified vulnerabilities, the testing techniques used, their potential impacts, and recommended remedial actions. For clarity and practicality, vulnerabilities are ranked by severity and risk, including evidence like screenshots and logs. More than just highlighting flaws, the report guides development and security teams in remediation and helps enhance the application’s security measures. It’s also crucial for compliance with regulatory standards and informs the organization’s future security strategies.
To learn more about penetration testing phases check out the related blog post.
