Desktop Application Penetration Testing Explained
Desktop Application penetration testing is a targeted security evaluation designed to pinpoint and mitigate vulnerabilities within desktop computing environments.
Such testing is vital for the protection of sensitive data housed on desktop machines, which frequently become the focus of cybercriminal activities because of their extensive usage across home and work spaces.
Through the emulation of actual cyber attacks, this form of testing reveals possible security flaws that might be leveraged by adversaries, thereby playing a key role in fortifying desktop systems against potential breaches.
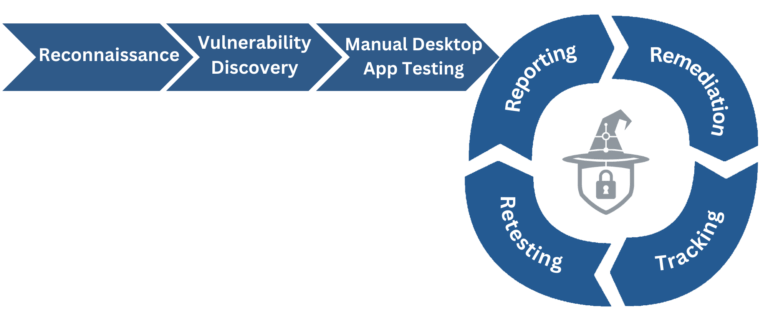
The process of desktop application penetration testing encompasses several stages, starting with the planning phase, where objectives and scope are defined. It is followed by reconnaissance, where testers gather information about the target system. The actual testing phase involves the identification of vulnerabilities through both automated tools and manual techniques. This phase may include testing for software flaws, misconfigurations, and vulnerabilities in operating systems and applications. Once vulnerabilities are identified, attempts are made to exploit them, mimicking the actions of an attacker to assess the potential impact.
In the concluding phase, the process culminates with a detailed report of the findings, outlining identified vulnerabilities, how they could be exploited, and suggested measures for fixing these issues. This thorough methodology guarantees the reinforcement of desktop systems against possible security incursions, safeguarding the data’s integrity and confidentiality.
Application and Business Logic Mapping
In the Application and Business Logic Mapping phase of desktop application penetration testing, testers examine the application’s workflow and functionality to identify how it manages business processes and user interactions. They focus on key aspects like input fields, authentication, and communication protocols, looking for vulnerabilities in the application’s logic and design, such as validation issues or business rule bypasses. This phase is vital for identifying logical flaws that automated tools may overlook, especially in unique, custom functionalities of the application.
This stage also involves understanding the application in its business context. Testers analyze how the application’s features align with its business objectives, identifying any logical inconsistencies that could be exploited. For example, in a financial application, the focus would be on transaction handling, account management, and data integrity, searching for vulnerabilities like unauthorized access or data manipulation. This comprehensive approach ensures the identification of both technical and business logic vulnerabilities, crucial for enhancing the security of the desktop application.
Automated and Manual Vulnerability Discovery
In the Automated and Manual Vulnerability Discovery phase of desktop application penetration testing, the process starts with automated tools like vulnerability scanners. These tools efficiently scan the application for known issues, such as outdated components and common security flaws, quickly providing an initial security assessment. However, automated scans may not detect complex or application-specific vulnerabilities.
The phase then progresses to manual testing, where testers’ expertise comes into play. They conduct in-depth analyses, including reverse engineering and code review, to find vulnerabilities that automated scans overlook, such as custom code flaws or business logic errors. This blend of automated and manual approaches ensures a thorough evaluation of the application’s security, uncovering both obvious and subtle vulnerabilities.
Manual Testing and Exploitation
In the Manual Testing and Exploitation phase of desktop application penetration testing, testers conduct in-depth investigations to find and exploit vulnerabilities that automated scans may have missed. They focus on critical areas such as user input, file handling, and security controls, using techniques like fuzzing and code injection to uncover subtle flaws in business logic and custom code. This phase is key for revealing vulnerabilities under abnormal conditions and assessing the application’s response to potential security breaches.
The exploitation stage involves applying these findings in real-world attack scenarios, actively exploiting weaknesses to gauge the potential damage, like unauthorized data access or system compromise. This approach not only confirms the vulnerabilities but also helps understand their real-world impact, guiding the prioritization of fixes and strengthening the application’s defense against advanced threats.
Reporting
In desktop application penetration testing, the reporting phase results in a comprehensive report that categorizes each discovered vulnerability by its severity and potential impact, aiding in prioritization for remediation. The report details the vulnerabilities’ locations, methods of discovery, and evidence, such as screenshots or logs, offering practical recommendations for security improvements. This report is critical for both immediate corrective actions and strategizing long-term security enhancements.
