Free Vulnerability Assessment
Pentest Wizard is offering a free vulnerability assessment of your assets.
Fill in the form below and schedule your free assessment. No strings attached.

What is a Vulnerability Assessment?
A vulnerability assessment is a systematic method used to identify, evaluate, and prioritize potential security weaknesses in an organization’s IT systems, networks, and applications. It involves scanning and analyzing various components of the IT infrastructure or applications to find vulnerabilities that cybercriminals could exploit. The primary goal is to give organizations a clear understanding of their security posture and help them address potential risks before they can be exploited.
During the assessment, specialized tools (such as Nessus, Burp Suite, and similar) are used to scan systems for known vulnerabilities, such as outdated software, misconfigurations, or weak passwords. These tools compare the current state of your systems against a database of known security issues.
By performing regular vulnerability assessments, organizations can proactively detect and address security weaknesses, thereby lowering the risk of data breaches and cyberattacks. This process ensures the integrity, confidentiality, and availability of essential information and systems, ultimately safeguarding the organization, its clients, and its reputation.
If you are looking for a penetration test instead, feel free to contact us and discuss the details.
How does it work?
1. Fill in the Form
You fill in the form located below with your contact details and we will get back to you on the shortest notice.
2. Schedule a meeting
We will schedule a meeting to discuss the potential start date of the vulnerability assessment and to answer any questions you might have.
3. Invitation to the Platform
We will prepare everything for the kick-off, and you will receive an email invite to access our platform.
On our platform, you can see all the details of your assessment, as well as all discovered findings in real-time.
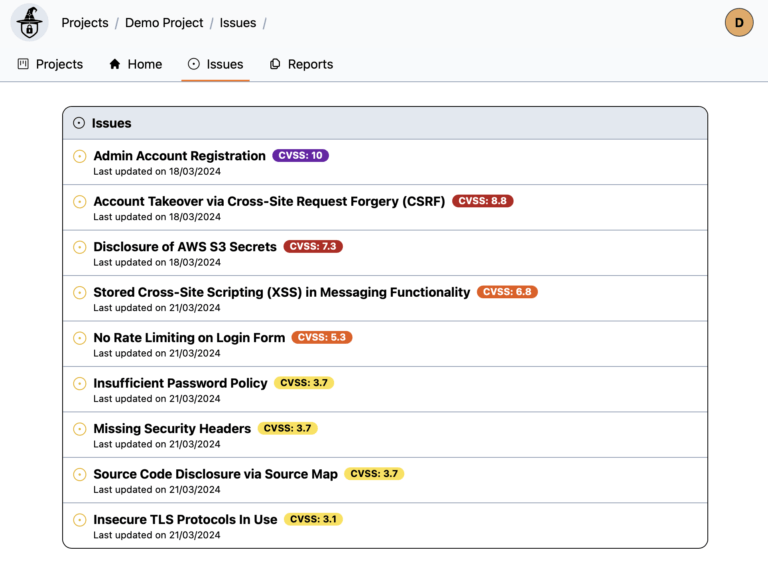
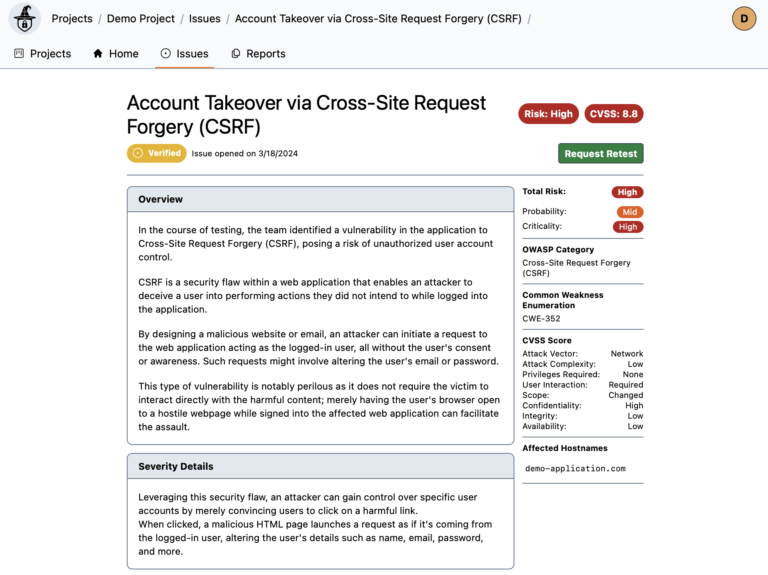
4. Final Report
At the end of the vulnerability assessment, typically within one week, you will receive a detailed assessment report. The report will contain details of each discovered vulnerability as well as our recommendations on how to remediate those vulnerabilities.
