Welcome to our guide on how to keep your web applications safe. In today’s digital world, it’s important for all businesses, regardless of their size, to prioritize web application security.
The number of cyber threats and attacks that specifically target web applications is on the rise, which means it’s absolutely necessary to have effective security measures in place. This is to ensure the protection of your sensitive data, customer information, and the overall reputation of your business.
In this guide, we will look at ways to keep your web applications secure. We will explain what web application security is and why it is important. We will also discuss the benefits of penetration testing, which helps identify vulnerabilities. Finally, we will provide strategies that you can use to protect your web applications. By following these practices, you can reduce the chances of security incidents and keep your web applications safe for both you and your users.
Understanding Web Application Security
Before we go into the important guidelines, let’s start by understanding what web application security means. It’s all about keeping web applications safe from different dangers and weaknesses that could put their reliability, privacy, and accessibility at risk.
Web applications can be at risk of various attacks, such as SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF), among others. These attacks can lead to unauthorized entry into sensitive information, alteration of web pages, or even total control over the system.
Web application security breaches can have serious consequences. They can damage your reputation, cause financial loss, result in legal issues, and make customers lose trust in your business. That’s why it’s crucial to prioritize the security of your web applications.
By doing so, you can protect your business and maintain a strong presence online.
The Importance of Penetration Testing
One of the most important parts of keeping your website safe is penetration testing. This is also called ethical hacking. It means that experts pretend to be hackers and try to find any weaknesses or vulnerabilities in your website.
Penetration testing is extremely important for several reasons. First and foremost, it helps you uncover any weaknesses or vulnerabilities in your web applications before cyber attackers have a chance to take advantage of them. By finding and fixing these problems ahead of time, you can greatly enhance the security of your web application and prevent any potential breaches.
Secondly, penetration testing helps you understand how well your current security measures are working. It allows you to see how well your web applications can defend against different types of attacks and lets you make adjustments to your security plan based on what you learn.
Regular penetration testing is highly recommended to ensure the ongoing security of your web applications. By conducting frequent tests, you can stay one step ahead of potential attackers and mitigate any emerging vulnerabilities promptly.
Best Practices for Web Application Security
Secure Coding Practices
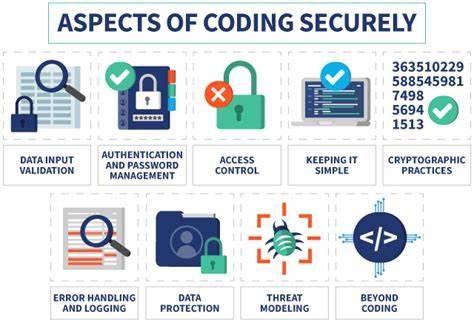
Ensuring the security of web applications relies on using secure coding practices. These practices, which are based on guidelines, help minimize the chances of adding weaknesses or vulnerabilities to the codebase. Here are some commonly recommended secure coding practices:
- Input Validation: Ensure that all information entered by users is validated and cleaned to protect against malicious attacks.
- Avoiding hardcoded credentials: Store sensitive information securely and don’t embed them directly into the source code.
- Implementing access controls: Ensure that only authorized users have access to specific functionalities or data.
- Regular code reviews: We carefully examine the code to find and address any possible security problems.
- Error handling: Create effective methods for managing errors to avoid the unintended disclosure of sensitive data.
By including safety measures during the creation of your website, you can ensure that it is strong and protected against cyber threats.
Authentication and Authorization
Ensuring the security of web applications involves two important aspects: authentication and authorization. Authentication is the process of confirming the identity of users, so only genuine users can access your web applications. By implementing strong authentication mechanisms, you can prevent unauthorized users from gaining access. Here are some recommended best practices for authentication:
- Encouraging Users to Create Strong Passwords:
We recommend using strong passwords that contain both uppercase and lowercase letters, numbers, as well as special characters. - Enabling multi-factor authentication (MFA): Ask users to provide extra verification by requesting a one-time password sent to their mobile device.
- To enhance security, we can set up a system that limits the number of times someone can try to log in before their account is temporarily disabled. This helps prevent unauthorized access by slowing down or blocking repeated failed login attempts.
Authorization controls determine what a user can do in your web application. Here are some effective strategies for managing authorization:
- The principle of least privilege means that users should only be given the necessary permissions to complete their tasks and nothing more.
- Regular access reviews involve regularly checking and removing access privileges that are not necessary. This is done to reduce the chances of unauthorized access to sensitive information.
- Role-based access control (RBAC) is a way to manage who can do what in a system. It involves assigning different roles to users and giving them permissions based on these roles.
By using secure login and access controls, you can greatly improve the safety of your web applications.
Input Validation and Data Sanitization
Input validation and data sanitization are crucial for preventing common web application vulnerabilities such as SQL injection and cross-site scripting. Some techniques for validating user input and sanitizing data include:
- Whitelist validation: Define a whitelist of acceptable characters and validate user input against this whitelist.
- Input length validation: Limit the length of user input to prevent buffer overflow attacks.
- Regular expression validation is a way to check if certain patterns, like email addresses or phone numbers, are valid.
- HTML encoding: Encode user-supplied data before displaying it on web pages to prevent cross-site scripting attacks.
By implementing robust input validation and data sanitization techniques, you can protect your web applications from various attacks that exploit input vulnerabilities.
Session Management
Proper session management is essential for web application security. Sessions allow web applications to maintain user state and track user interactions. Some best practices for secure session handling include:
- Session expiration: Set a reasonable session timeout to ensure that inactive sessions are automatically terminated.
- Secure session storage: Use secure storage mechanisms, such as HTTP-only cookies or server-side sessions, to prevent session hijacking.
- Session fixation prevention: Generate a new session identifier after a successful login to prevent session fixation attacks.
- Session revocation: Provide a mechanism for users to manually revoke their sessions, such as a logout functionality.
By following these recommended methods, you can stop unauthorized people from accessing user accounts and keep confidential user information safe.
Secure File Uploads
File uploads can pose significant security risks to web applications if not handled correctly. Some best practices for secure file uploads include:
- Validate file types: Only allow specific file types to be uploaded and reject any files with potentially malicious content.
- Set a restriction on the size of files: By establishing a limit on the maximum file size, we can prevent malicious attempts to disrupt services or abuse storage space.
- Secure file storage: Store uploaded files outside the web root directory to prevent direct access and potential execution of malicious files.
- Regularly scan uploaded files: Implement antivirus or malware scanning to detect any potentially harmful files.
By following these best practices, you can ensure the secure handling of file uploads in your web applications.
Security Headers and HTTPS

Implementing security headers is an effective way to enhance web application security. Security headers provide additional instructions to web browsers on how to handle and protect web content. Some essential security headers include:
- Content Security Policy (CSP) determines which sources are permitted to display different types of content, such as scripts, stylesheets, and images.
- X-XSS-Protection: Enables the browser’s built-in XSS protection mechanisms.
- X-Frame-Options: Prevents clickjacking attacks by controlling how web content can be embedded in iframes.
- Strict Transport Security (HSTS) ensures that all communication with your web application is secure by making sure that the website uses HTTPS.
In addition to implementing security headers, enabling HTTPS on your website is crucial for secure communication between your web application and users. HTTPS encrypts data in transit, preventing eavesdropping and tampering.
Regular Patching and Updates
It is important to keep your web applications updated to ensure their security. Software companies often release patches and updates to fix security weaknesses and bugs. Here are some recommended ways to regularly update and patch your applications:
- Keep track of databases that identify security weaknesses in the software and libraries utilized in your web applications in order to stay updated and informed about any potential threats.
- Creating a system for managing patches: Set up a process to quickly apply security patches and updates to your websites and online applications.
- Testing updates in a sandbox environment: Before applying updates to production environments, test them in a controlled environment to ensure compatibility and stability.
To keep your web applications safe, it’s important to stay updated with patches and updates. This way, you can protect your applications from any known weaknesses and reduce the chances of them being taken advantage of by hackers.
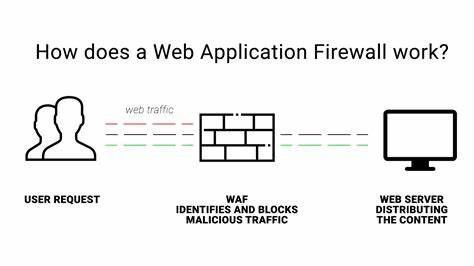
Web Application Firewall (WAF)
A Web Application Firewall, often called a WAF, is a really important safety tool that can add an extra layer of protection to your online applications. Imagine it like a security guard, stopping and checking all incoming traffic to block out any harmful requests. Here are some benefits of using a WAF:
- A Web Application Firewall (WAF) offers protection against common attacks that can occur on websites. It has the ability to identify and prevent harmful activities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
- Rate limiting and traffic filtering: A Web Application Firewall (WAF) can control the amount of requests coming from a specific IP address or block requests that match particular patterns or signatures.
- Virtual patching: A WAF can provide temporary protection against known vulnerabilities until an official patch is available.
When deciding on a Web Application Firewall (WAF), it’s important to think about things like how easily it can be set up, the options for customizing it to your specific needs, and whether it will work well with your web application setup. By implementing a WAF, you can greatly improve the security of your web applications.
User Education and Awareness

While technical measures are essential for web application security, user education and awareness also play a crucial role. Users are often the weakest link in the security chain, and their actions can inadvertently lead to security breaches. Some strategies for raising user awareness about security best practices include:
- Security training and awareness programs: Provide regular training sessions and resources to educate users about common security threats and best practices.
- Phishing simulations: Conduct simulated phishing campaigns to test user awareness and provide immediate feedback and training.
- Clear and concise security policies: Establish and communicate clear security policies that outline acceptable use and security practices.
By fostering a strong commitment to security in your organization and equipping users with the skills to recognize and handle potential dangers, you can greatly enhance the overall protection of your web applications.
Conclusion
Protecting your web applications is incredibly important in today’s digital world. By following the suggestions in this guide, you can reduce the chances of security breaches and keep your valuable data, customer information, and good reputation safe.
It’s important to understand that keeping your website secure is an ongoing task. Make sure to regularly check and improve your security measures, carry out tests to identify any weak points, and stay updated on new threats and vulnerabilities. By placing a high priority on web application security, you can guarantee the long-term success of your online presence.
