In today’s modern age, where online threats are growing rapidly, it is incredibly important for organizations to focus on protecting their networks. One of the best ways to ensure the safety of your network is through penetration testing. In this article, we will discuss the significance of penetration testing in uncovering weaknesses and keeping your network secure.
Understanding Penetration Testing
What is penetration testing?
Penetration testing, or ethical hacking, is like a health check-up for your computer network or system. It’s a way of finding any weak spots that could let hackers in. It works by pretending to be a hacker attack to see how well your system would hold up. Doing these checks helps organizations find and fix any problems before real hackers can take advantage of them.
How does penetration testing work?
Penetration testing typically follows a systematic approach that involves several phases. The process begins with planning and scoping, where the objectives and goals of the test are defined.
Next, reconnaissance and information gathering are conducted to gather intelligence about the target.
Vulnerability scanning and assessment are then performed to identify potential weaknesses. Once vulnerabilities are identified, the penetration tester exploits them to gain access to the network.
Finally, a detailed report is generated, outlining the findings and recommendations for remediation.
The different types of penetration testing
There are different types of penetration testing, which depend on what is being tested. One crucial aspect to consider is external penetration testing, which focuses on assessing threats from outside the network.
Here are some examples of commonly used types of penetration testing:
- Web application penetration testing is all about finding weaknesses or vulnerabilities in web applications. These vulnerabilities, if not fixed, can be used by malicious individuals or attackers to harm the application or gain unauthorized access to it.
- Mobile application penetration testing involves assessing the security of mobile applications to ensure they are resistant to attacks.
- Network penetration testing is a process that aims to identify vulnerabilities in a network’s infrastructure. These weaknesses, if left undiscovered, could potentially be exploited by malicious attackers.
- Active Directory penetration testing aims at discovering weaknesses in an organization’s Active Directory setup, which is commonly used for logging in and controlling access for users.
- Phishing simulations involve testing an organization’s susceptibility to phishing attacks by simulating real-world scenarios.
The benefits of conducting penetration testing
Conducting regular penetration tests offers several key benefits for organizations:
- Identifying Weaknesses
Pentesting helps organizations find vulnerabilities in their network and system infrastructure. By understanding these weaknesses, organizations can take action to fix them before bad actors can exploit them. - Mitigating Risks
By uncovering vulnerabilities and addressing them, organizations can reduce the risk of data breaches, financial losses, and reputational damage. - Improving Network Security
Pentesting offers valuable insights into how well an organization’s security measures are working. By finding weak points in their defense system, organizations can boost their overall security and better safeguard their network.
How does penetration testing help ensure network security?
Penetration testing is an important part of safeguarding network security. It helps identify vulnerabilities and weaknesses that unauthorized individuals could exploit. Conducting penetration tests regularly ensures a strong defense against potential threats.
By performing these tests, potential security threats can be addressed and proper measures can be taken to prevent them.
- Identifying vulnerabilities through penetration testing
By conducting thorough penetration tests, organizations can identify vulnerabilities that may go unnoticed by traditional security measures. This includes weaknesses in software, misconfigurations, and poor security practices. - Mitigating risks and preventing potential cyber attacks
By addressing vulnerabilities discovered during penetration testing, organizations can reduce the risk of successful cyber attacks. This proactive approach allows organizations to fix vulnerabilities before they are exploited by malicious actors. - Enhancing network security with penetration testing
Penetration testing offers important insights into how well an organization’s security measures are working. It helps identify areas of vulnerability, so organizations can take necessary steps to reinforce their defenses and safeguard against future cyber-attacks.
Types of Penetration Testing
Web Application Pentesting
Web application penetration testing is a way to check the security of web applications. It involves finding weaknesses like SQL injection, cross-site scripting (XSS), and insecure direct object references. When organizations do web application penetration testing, they can make sure their web applications are protected and can handle attacks.
Mobile Application Pentesting
Mobile application penetration testing is a way to check how secure a mobile app is. It involves looking for any weaknesses in how the app stores data, encrypts information, and communicates with other devices. By doing this testing, companies can make sure their apps are safe and protect personal information from being misused.
Network Pentesting
Network penetration testing is a way of testing the security of an organization’s network infrastructure. This involves checking things like routers, switches, firewalls, and other devices that help the network function properly. By doing this testing, organizations can find any weaknesses in their network that attackers could potentially use to gain access without permission.
Active Directory Dentesting
Active Directory penetration testing focuses on assessing the security of an organization’s Active Directory environment. This includes identifying vulnerabilities such as weak passwords, misconfigurations, and privilege escalation opportunities. By conducting active directory penetration testing, organizations can ensure the security of their user authentication and authorization systems.
Phishing simulations
Phishing simulations involve testing an organization’s susceptibility to phishing attacks. This includes sending simulated phishing emails to employees and assessing their responses. By conducting phishing simulations, organizations can identify vulnerable individuals and provide targeted training to mitigate the risk of successful phishing attacks.
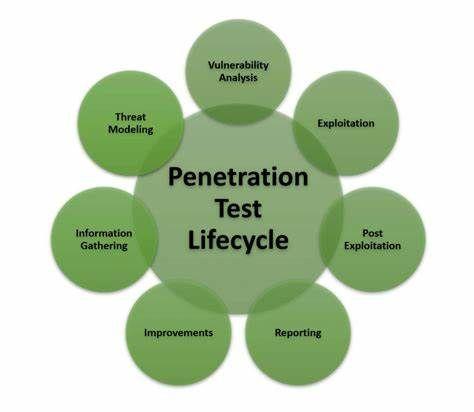
The Process of Penetration Testing
Planning and scoping the penetration test
The first step in the penetration testing process is to plan and outline what we want to achieve. This includes setting goals and determining the boundaries of the test. We also need to establish the rules and expectations for the testing. Making sure that both the organization and testing service provider understand each other is crucial during this phase.
Reconnaissance and information gathering
During this phase, the penetration tester gathers information about the target organization. This may include gathering publicly available information, such as domain names, IP addresses, and employee details. The goal is to gain insights into the organization’s infrastructure and identify potential entry points for attacks.
Vulnerability scanning and assessment
During this phase, the penetration tester utilizes specific tools to examine the target network or system for any weaknesses. This involves performing automated scans to check for vulnerabilities and conducting manual assessments. The objective is to uncover any potential weaknesses that could be taken advantage of.
Exploitation and gaining access
After identifying weaknesses, the penetration tester tries to break into the target system to gain unauthorized access. This may involve using different hacking techniques and tools to get around security measures. The purpose is to imitate real-world attacks and evaluate how well the organization’s defenses hold up.
Post-exploitation and reporting
After gaining access, the penetration tester assesses the extent of the compromise and the impact of the attack. This includes identifying sensitive data that could have been accessed and assessing the overall security posture of the organization. A detailed report is then generated, outlining the findings, recommendations for remediation, and steps to improve the organization’s security posture.
Best Practices for Penetration Testing
Setting clear objectives and goals
Before starting a penetration test, it’s crucial to set clear goals and objectives. This will help us to concentrate our efforts and get useful outcomes that can be used to enhance the security of the network.
Collaborating with stakeholders
Effective penetration testing requires collaboration with stakeholders within the organization. This includes IT teams, system administrators, and other relevant personnel. By involving the right stakeholders, organizations can ensure that the test aligns with their security requirements and objectives.
Utilizing a comprehensive testing methodology
A comprehensive testing methodology is essential for conducting effective penetration tests.
This includes using a combination of automated tools and manual assessments to identify vulnerabilities. By utilizing a comprehensive approach, organizations can uncover a wider range of vulnerabilities and assess the overall security posture of their network.
Keeping up with the latest hacking techniques and tools
To stay safe from possible danger, it’s key to always be up-to-date with the newest ways criminals are trying to hack into systems. This includes learning about new weaknesses they might exploit, methods they might use, and trends in the world of online security. By keeping informed, businesses can more effectively guard their computers and respond to any dangers before they become serious issues.
Regularly performing penetration tests
Ensuring the security of a network is a continuous effort that involves regularly testing it for weaknesses. This is important to maintain a strong level of security. By conducting these tests, organizations can discover any new vulnerabilities that may appear as a result of system changes or updates. This practice helps to keep the network secure and protected against potential attacks.
Conclusion
Penetration testing is crucial for keeping your network secure. It involves regularly testing your network to find vulnerabilities, assess risks, and strengthen your defenses. With the ever-growing cyber threats today, it’s essential to be proactive and protect your network. Stay ahead of potential threats by regularly incorporating penetration testing into your security strategy.
